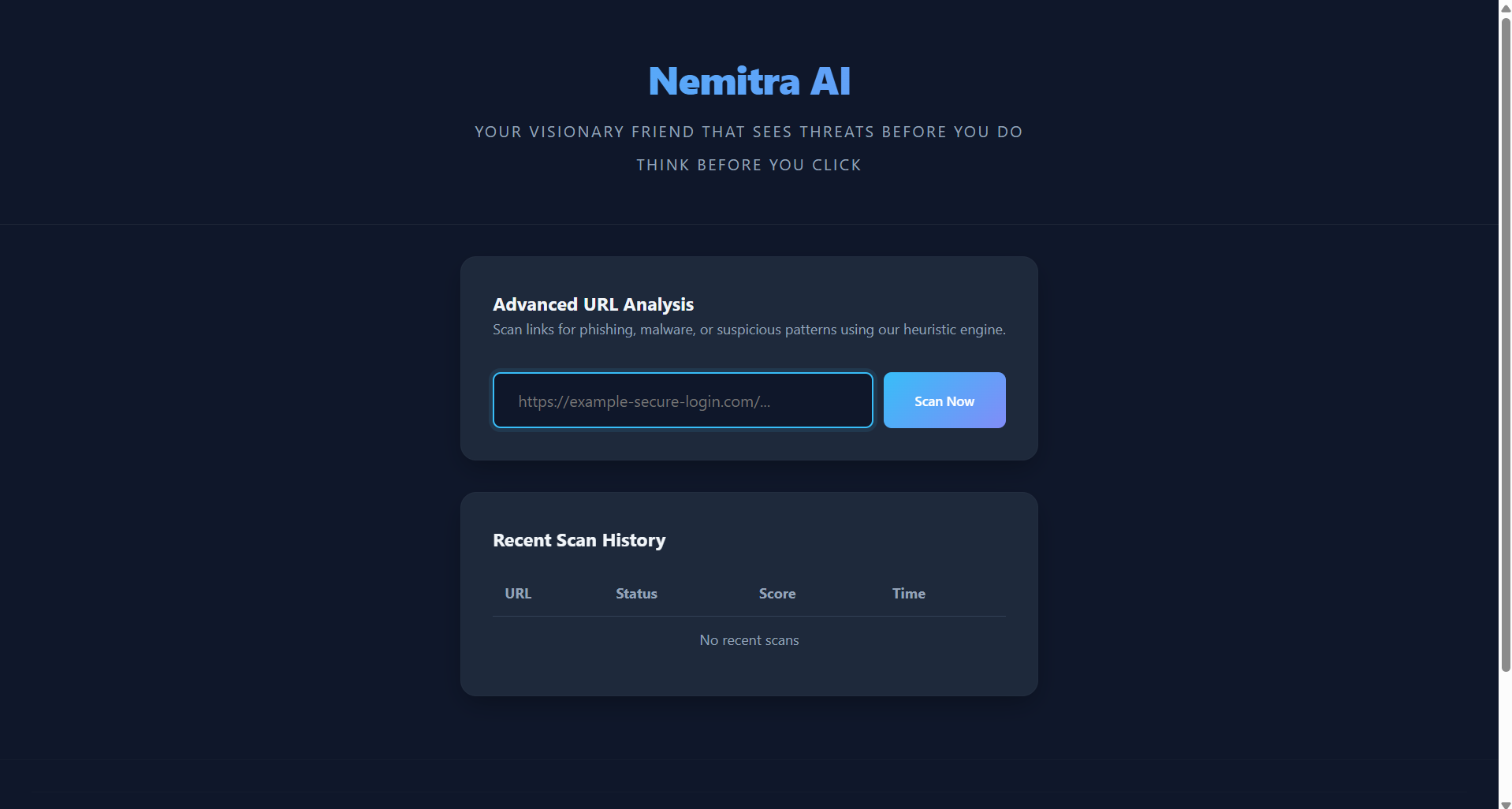
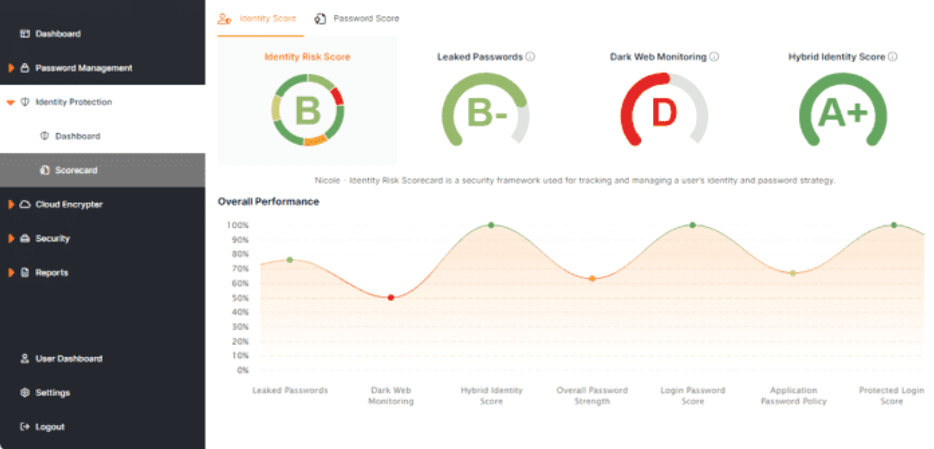
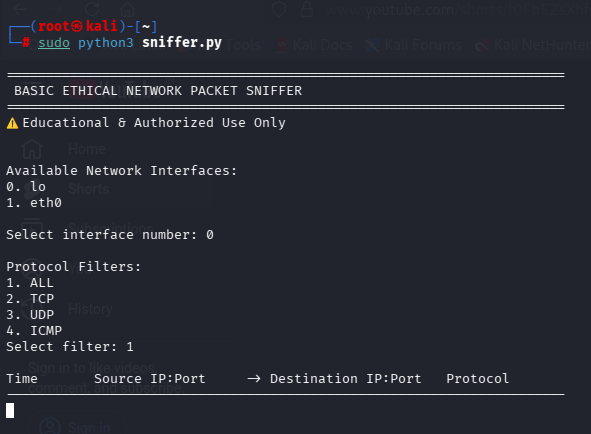
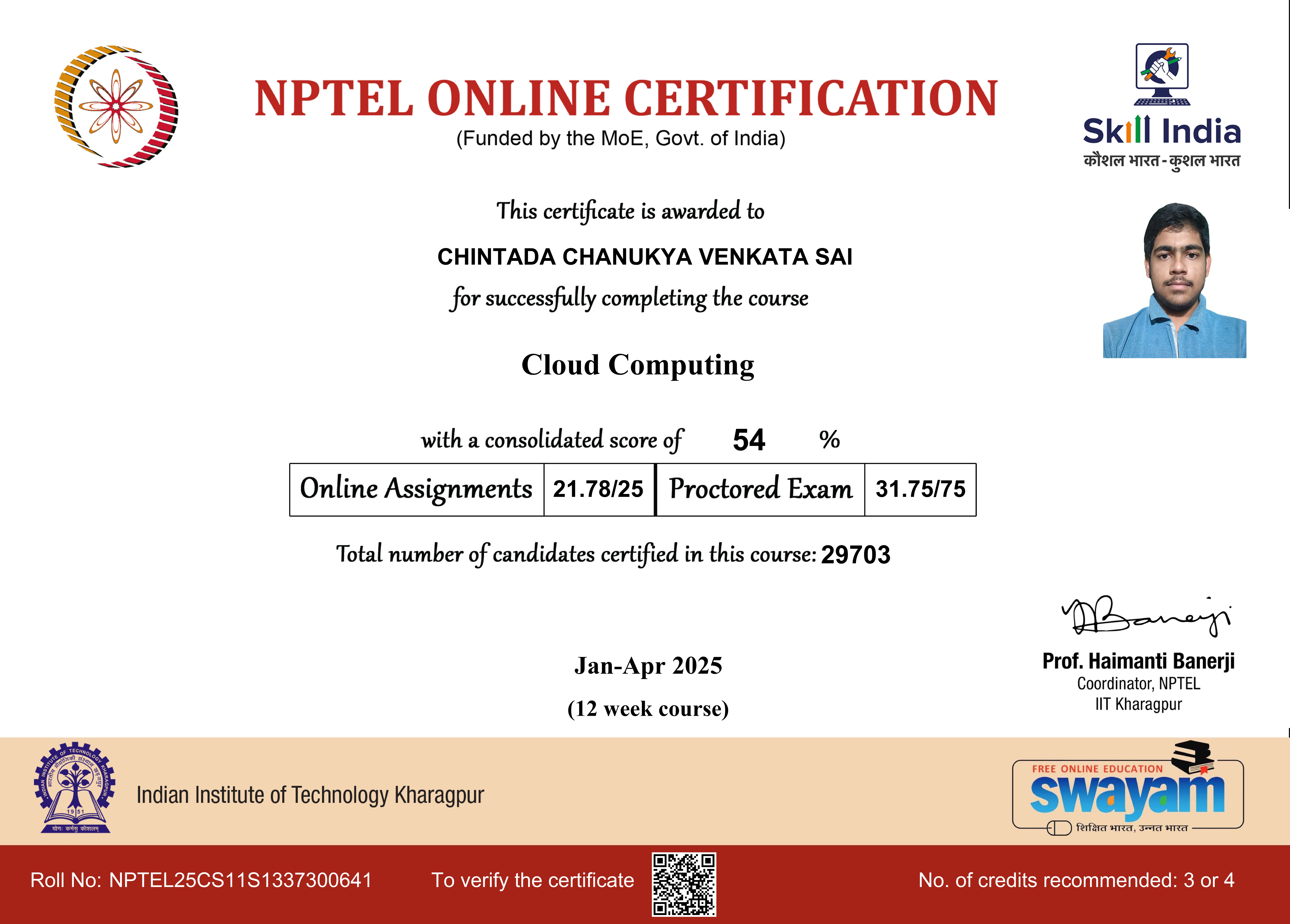
Hello, I am
Chanukya Venkata Sai Chintada
I am a Computer Science and Engineering undergraduate with a strong interest in
Cybersecurity, system security, and
secure application development.
Currently, I am pursuing my B.Tech in Computer Science, where I have built a solid foundation in
programming, operating systems, computer networks, and Linux administration.
Alongside academics, I actively upskill through hands-on labs, certifications, and projects
focused on cybersecurity defense, cloud computing, and Linux system administration.
My career goal is to work in Blue Team / SOC Analyst roles, where I can contribute to
monitoring, detecting, and responding to security incidents.
I am also exploring ethical hacking and penetration testing to strengthen my defensive
mindset by understanding attacker techniques.
I combine theoretical foundations with practical security implementation, actively building projects,
documenting learning, and continuously improving through labs, certifications, and real-world practice.